The pace of technological innovation is faster today than ever before. If you’ve been looking for a career change in the IT field but are not sure which career to pursue, you’ve landed at the right place! Welcome to List Of Top 10 Trending Technologies in 2022.
To survive in this competitive world, up-scaling oneself is the need of the hour. Here are the top 10 trending technologies, which are expected to acquire a huge market in 2022-2023 and beyond.
Top 10 Trending Technologies in 2022 – 2023
- Artificial Intelligence and Machine Learning
- Data Science
- Cybersecurity
- Blockchain
- AWS
- DevOps
- Salesforce CRM
- Full Stack Development
- Virtual Reality and Augmented Reality
- Robotic Process Automation
- Artificial Intelligence and Machine Learning:
Artificial Intelligence is defined as the process of developing intelligent machines that can be able to behave like human. It is basically an artificial intelligence machine that is able to tackle problems that are typically handled by humans by using their inherent intelligence.
Artificial Intelligence is achieved through the development of robots and machines that behave like human beings and has been in an enormous demand in recent years. Nowadays, Artificial Intelligence is assisting many businesses and organizations in more effective implementation of their strategies which is why AI is now the focus of attention for numerous top-quality firms. It is recognized as being among the fastest growing technologies of the current era that is capable of offering the highest salaries for the entire country. As of now, there are more than 20,000 open positions for various positions within the area of Artificial Intelligence.Hence it is increasing and is expected to increase in the near future. In light of this, a lot of professionals are looking to make a career in this field and are searching for training classes on AI as well as ML. This is precisely the reason Great Learning has designed a collection of these incredible training courses for AI that will help you reach your goals faster.
- Data Science
Data Science Data Science is an amalgamation of techniques that are that are derived from data analysis, statistics and machine learning that are trained to collect and analyze massive amounts of unstructured and structured data.
An Data Scientist an individual who must prepare massive quantities of massive data for analysis, create complex algorithms for quantitative analysis to arrange and synthesize the data, and present the findings in captivating visualizations for senior management. The Data Scientist enhances business decision making by providing greater speed and greater direction to the whole process.
A Data Scientist is someone who is passionate about having fun with numbers as well as numbers. A strong analytical approach and a strong understanding of the industrial world is the key skill needed in the job of a Data Scientist. They must have an above-average communication skill and be proficient in communicating technical ideas to non – technical individuals. Data Scientists require a solid base of Statistics, Mathematics, Linear Algebra, Computer Programming, Data Warehousing, Mining, and Modeling to develop successful algorithms. They should be skilled using tools like Python, R, R Studio, Hadoop, MapReduce, Apache Spark, Apache Pig, Java, NoSQL database, Cloud Computing, Tableau and SAS.
In this world of data-driven, Data Science certification in hyderabad will prepare you to meet the increasing demand for Data Science skills and technology in the most prestigious industries. There is an enormous potential for career advancement for those interested in Data Science and this program is among the most thorough Data Science that is available in the present. This program in Hyderabad is specifically designed for novices and professionals who wish to establish an impact in this rapidly growing field. This course will equip students with the necessary logical and pertinent ability to program databases. They are able to develop basic machine-learning algorithms such as K-Means Clustering Decision Trees, and Random Forest to tackle problems and present the results efficiently. In the course of three months, the students will study the fundamental methods such as Statistical Analysis, Regression Analysis, Data Mining, Machine Learning Forecasting, Text Mining and creating scripting algorithms to achieve the same using Python as well as R Programming. Learn the fundamental principles of Neural Networks, and learn about Deep Learning Black Box techniques such as SVM.
Data Science is an amalgam of methods derived from statistics, data analysis, and machine learning that are trained to extract and analyze huge volumes of structured and unstructured data.
A Data Scientist is a researcher who has to prepare huge volumes of big data for analysis, build complex quantitative algorithms to organize and synthesize the information, and present the findings with compelling visualizations to senior management. A Data Scientist enhances business decision making by introducing greater speed and better direction to the entire process.
A Data Scientist must be a person who loves playing with numbers and figures. A strong analytical mindset coupled with strong industrial knowledge is the skill set most desired in a Data Scientist. He must possess above average communication skills and must be adept in communicating the technical concepts to non – technical people. Data Scientists need a strong foundation in Statistics, Mathematics, Linear Algebra, Computer Programming, Data Warehousing, Mining, and Modeling to build winning algorithms. They must be proficient in tools such as Python, R, R Studio, Hadoop, MapReduce, Apache Spark, Apache Pig, Java, NoSQL database, Cloud Computing, Tableau, and SAS.
In this data-driven environment data science certification course in Hyderabad prepares you for the surging demand of Data Science skills and technology in all the leading industries. There is a huge career prospect available in the field of data science and this programme is one of the most comprehensive Data Science in the industry today. This course in Hyderabad is specially designed to suit both data professionals and beginners who want to make a career in this fast-growing profession. This training will equip the students with logical and relevant programming abilities to build database models. They will be able to create simple machine learning algorithms like K-Means Clustering, Decision Trees, and Random Forest to solve problems and communicate the solutions effectively. In three months, students will also explore the key techniques such as Statistical Analysis, Regression Analysis, Data Mining, Machine Learning, Forecasting and Text Mining, and scripting algorithms for the same with Python and R Programming. Understand the key concepts of Neural Networks and study Deep Learning Black Box techniques like SVM.
- Work with various data generation sources
- Perform Text Mining to generate Customer Sentiment Analysis
- Analyse structured and unstructured data using different tools and techniques
- Develop an understanding of Descriptive and Predictive Analytic
- Apply Data-driven, Machine Learning approaches for business decisions
- Build models for day-to-day applicability
- Perform Forecasting to take proactive business decisions
- Use Data Concepts to represent data for easy understanding
- Cybersecurity:
Cyber Security is a field that is developing and growing exponentially. Cyber Security is gaining much attention. as we all know that the tech sector has made massive strides in the 21st century thanks to innovations that have brought the entire world into our reach. While it has made our lives unquestionably simpler, it has also opened up a whole new world of opportunities for criminals that could take advantage of the data that the world has posted online for unintentional motives. That’s the place where Cyber Security comes in.
The most appealing part is that if one is proficient in the methods and tools, and even have basic knowledge of how to use it, the cyber world will be welcoming the person with all-inclusive arms.
As a result of the pandemic it is a higher chance for data leaks, breaches and cyber crime that could be detrimental to businesses across all sectors. The need for experienced cybersecurity experts is critical with each passing day, new threats are being invented which can be more destructive than previous attacks.
The rising threat of cyber crime requires experienced cybersecurity experts to safeguard both individuals and organizations. This influx of demand with a shortage of talent supply has resulted in very high salaries and lucrative benefits for applicants who meet the requirements. This makes cybersecurity an ideal area for those looking to develop vibrant and effective careers.
There are many opportunities to start or advance career options in cybersecurity. In the end, Cybersecurity is no more a question of ‘if it’s a matter of “when.’
Let’s explore the various career possibilities with regard to cybersecurity that suit those enthusiastic and are interested in the field.
- IT Security Consultant
- Security Systems Administrator
- IT Security Engineer
- Ethical Hacker/Penetration Tester
- Compliance and Auditing
- Forensics Analyst/Investigator
- Incident Analyst/Responder
- Chief Information Security Officer
These are just a handful of titles of the many available in the field. If you’re passionate and the right training work, you can be a successful career in cybersecurity.
- Blockchain:
In today’s digital world where everything has changed a lot from tip to toe, blockchain technology has entered into the lives of the common man with a rising number of uses.
In layman’s terms, block chain is referred to as Distributed Ledger Technology, which makes any digital asset unalterable and transparent through the use of decentralization.
It has become useful for people working in the financial sector as it allows users to access and conduct transactions without any involvement of an unknown person. By encrypting users’ information, these transactions are carried out without any hindrances and for a long period of time.
Its security makes theft considerably more difficult because each cryptocurrency consists of its own unique number which is linked to only one owner.
To make a career in the blockchain is not everyone’s cup of tea, but with the right guidance, one may learn how to secure a bright future and, for that, the first and foremost thing is to learn the fundamentals of blockchain technology and collaborative approach.
The most important skill that one should know about is the collaborative approach, which helps one to understand the market activities and strategies easily, which makes you stand in the long run.
Commenting on career opportunities in blockchain, Meenakshi Sharma, Financial Advisor said, “Every job comes with some definite skills that are needed to excel on the job. When it comes to the blockchain, it’s black and white. You either have it or you don’t and to understand the slight difference is very important to take you in the industry.”
As blockchain is termed as one of the fastest-growing skill sets, the number of jobs is coming up at a certain pace. That is why blockchain professionals’ salaries are higher than IT professionals. Despite the fact that there are many career opportunities, people are still not very aware of them.
The demand for blockchain professionals is there in every sector, like the BFSI sector (Banking, financial services, and insurance), healthcare, supply chain, etc. One can find a job as a Blockchain developer, Blockchain quality engineer, Legal consultant, designer, project manager, and product manager, etc.
“Blockchain is a technology that will continue to be around for a long time and it’s a place people can build a career around.”
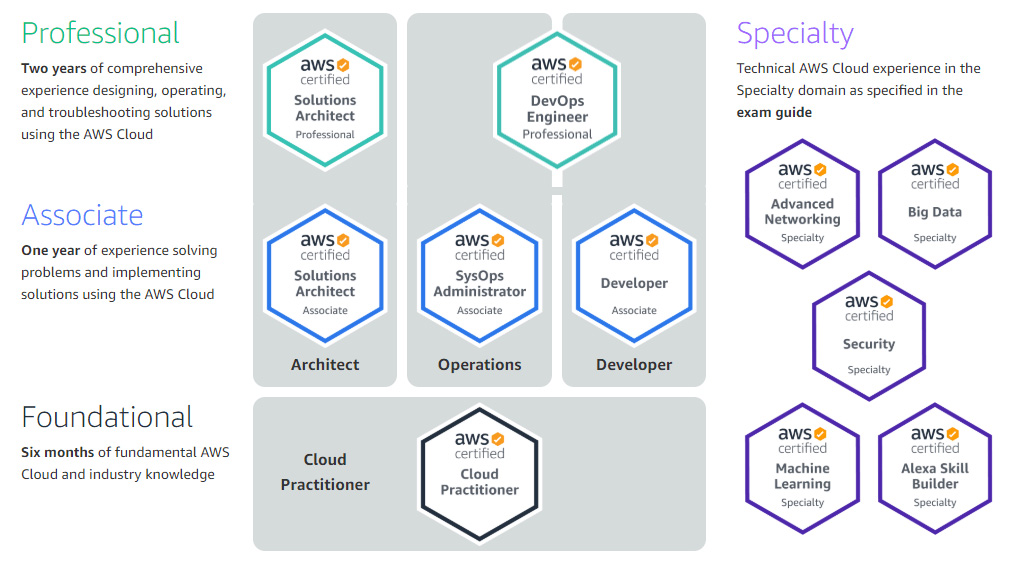
- AWS (Amazon Web Services):
The market for cloud services is growing quickly and is a significant chance for both the Amazon IT and retail giant. AWS has been playing a growing function in the cloud service sector and has emerged as an important source of revenue for Amazon. The year 2013 was the most successful for AWS. AWS generated revenues worth less than three billion U.S. dollars, a amount that has since risen and now stands at more than 25 billion U.S. dollars as of the year 2018. This is the ideal moment to get involved and begin your career in AWS. This article we’ll talk about AWS certifications and how it’s will help your career prospects in the Larger organizations that require cloud-based capabilities are usually devoted to specific solutions offered by service providers such as AWS. These companies have a wide range of expertise, which are regularly updated. This is why it is crucial to be updated to improve your career.
AWS is the leader with cloud computing. No matter if you’re an online developer or database, system administrator, Big data analyst, or IoT developer, the chances are that you’ve utilized the cloud computing service. Its AWS Certification helps you pursue career paths such as AWS Solutions Architect AWS Engineer, DevOps Engineer, Cloud Architect among others.
To take advantage of this opportunity, you must undergo well-organized AWS training that is updated with a program that meets current requirements of the industry and the best methods. In addition to a solid understanding of the theory it is essential to be involved in a variety of real-world projects and also work on various options for computing, storage and more.
In addition, you require the guidance of an expert who is working in the field and is tackling real-world challenges or you’d like to have immediate access to the latest information.
AWS Architecture Course is the first step to beginning your journey with Amazon Web Services cloud learning. This certification will help you become familiar to Amazon Web Services’ AWS platform and its core services. Learning courses that are certified by approved training institutes can boost your job prospects if decide to earn the highest-end AWS certification in your account.
The best way to master AWS Training to prepare you for the future, Nexson IT Academy providing AWS Classroom and Online Course that provide the most practical and effective training.
- DevOps
There are many advantages when you adopt an DevOps culture. The systems are developed faster and at a lower cost, and are typically of higher quality. The industry experts claim that DevOps is the most efficient way to run technology-intensive companies, which, according to some is the case for nearly all businesses currently.
The need for DevOps is increasing in the industry, which has led to a growing need for a competent DevOps team. Nearly every business is using cloud services in their operations, they require skilled professionals. If you are from an IT background, then learning DevOps is a must to begin your career.
DevOps is a promising field with a variety of solutions to IT issues. There is no question the fact that DevOps experts are paid well and committed. DevOps is an excellent strategy that is currently being used by numerous IT businesses to offer efficient and speedier solutions to their customers.
Before tackling the necessity to learn DevOps first, it is essential to understand the definition of DevOps is. DevOps is a method or method of practice that brings together the development team with the IT team to work together during the entire development process to ensure that the entire team is on the same team. It assists in reducing your SDLC (software development life cycle) and helps ensure the development of top-quality software.
Note: Devops will Also Add-On to the top skills like AI and ML
If you are looking to learn from top DevOps professionals, take a look at the DevOps Training at Nexson IT Academy.
- Salesforce CRM:
Salesforce specialists are in high demand, as businesses are seeking certified experts in this field. The statistics show that more than 60 percent of Salesforce implementations are a challenge in one way or other, usually creating a negative experience, increasing the need for a skilled team. Salesforce can impact changes made by employees, both in terms of the procedures to follow and as well as their behavior and expectations. This is why it is imperative to have an unbeatable adoption led by a competent team.
What makes an Salesforce certification so valuable?
- Employers who employ experts with a high level of certification typically have flawless deployments
- The the demand for Salesforce is increasing as is the demand for Salesforce certified professionals is also growing.
- Being certified can help professionals enhance their careers
- To increase your chances of being a marketable candidate on your IT job market
- In the present, more and more employers or clients require that their employees have an appropriate level of training in Salesforce.
Companies from all over the world have been growing and prospering with the renowned Salesforce’s platform. Highly respected individuals with a deep understanding about Salesforce and Salesforcetools and related software have a significant and vital part in governing the company’s operations. Everything (Sales HR, marketing Customer Service, etc.) within a company is created using Salesforce which is requiring employees to accomplish their work by training Salesforce expertise and knowledge.
If you’ve decided to begin your Salesforce career You are reading this article. However the question “Where do I go? What should I choose?” comes to the mind immediately.Though this question appears to be important however, the real answer is straightforward and is within you . Your own abilities and traits define your ability to choose the best route of Salesforce.
Nexson IT Academy Offers a specifically onine and classroom-based training. This course lets you gain a complete understanding of Salesforce’s Salesforce platform through understanding the most important aspects of Salesforce.
Administrator and developer foundational topics. New batches are starting soon, so do enroll now. Visit the link below.
- Full Stack Development
From large companies to smaller ones, careers are as lucrative as ever, and the need is expected to increase. In reality, jobs that require software comprise a portion of the most in-demand jobs.
The term “Full Stack Developer” refers to one who works on the Back End (or server side of the application, as well as the Front End which is the client side. Full Stack developers must be proficient in a broad range of programming niches, ranging from graphic design to databases and UX/UI management to succeed in their job. They’re an agile, always and are always ready to help to assist.
Coding careers are typically classified into three distinct specific areas:
- Full-stack developer
- Front-end developer
- Back-end developer
When is a Full-Stack Developer Required?
It is contingent on the scale and size of the program. For example, an independent group of gamers made up of a handful of people making a small simulator may include a Back End Developer and a Front End Developer, which could be all they require to develop. If they’re smaller there could be a Full Stack Developer, who manages the entirety of the application. However an application that is large with a strong possibility of scaling will require a variety of people working on it -for example, Back End, Front End as well as Full Stack Developers.
There’s never been an ideal time to be the Full Stack Developer, but you might be in a bind, wondering how you can get started in the market. You may need to improve your skills and demonstrate your credentials to become a Full Stack Developer or are looking to build connections within your area of expertise, If you’re looking for an instructor, Nexson IT Academy could be the best place to Learn.
- Virtual Reality and Augmented Reality
Virtual Reality (VR) and AR and augmented reality (AR) are both exciting possibilities for the future of marketing, gaming education, e-commerce as well as many other areas. Both technologies are recognized for their rich experience that combines two worlds: a virtual and real world with enhanced 3D-like visuals. While it is easy to confuse both, they have notable distinctions.
What is AR?
Nearly everyone using a smartphone has the ability to use augmented reality, which makes it more effective than VR as a marketing or gaming instrument. AR transforms the ordinary physical world into a vibrant visual world by projecting virtual images and characters on a phone’s camera or video player. Augmented reality adds to the real-world experience of the user.
What is VR?
Virtual reality elevates these components to the next dimension by creating an entirely computer-generated model of an alternative world. Virtual reality can be a resonant simulation that can recreate virtually any kind of visual or physical space possible for the user with the help of special equipment like headsets, sensors, computers and gloves.
What is the difference between the Two?
The difference among VR and AR depend on the hardware they require as well as the experience itself
AR is based on real-world settings and VR is entirely virtual.
AR users are able to be in control of their position on the ground. Virtual reality users can be controlled by the system.
VR is a must-have however, AR can be used via smartphones.
AR can enhance both the real and virtual world. VR only improves the fictional reality
Opportunities are available in VR and AR are in VR as well as AR Industry
These emerging technologies provide endless opportunities to companies and workers. By 2022 The AR as well as VR industry is expected to increase to $209.2 billion. VR and AR are changing industries through the development of hardware and software graphics design research, and many more.
Careers in high demand for in the field of developing and making improvements to VR and AR technologies include:
- Software engineering and development
- Project management
- Software maintenance
- Graphic design
Since virtual reality and virtual realities become increasingly integrated into the way we play, work, and study, the market is only going to continue to expand. The digital design course at Tulane School of Professional Advancement integrates design with cutting-edge technology to keep students on the cutting-edge of these fields while transforming their passion into a profession.
- Robotic Process Automation
The world RPA market is projected to grow to USD 10.7 billion by 2027.
As demand of automation technology, the need for highly skilled RPA experts is also rising. The combination of digital and human capabilities in RPA will result in many different and exciting career options. According to a study it is estimated that 2 lakh jobs in RPA will become available in India in 2021.
There’s never been a better time to think about the possibility of a career in RPA. These are the three main reasons to consider for a job in RPA.
Three reasons to consider an RPA career
Reason 01: Rapid adoption RPA across diverse industries
RPA assists businesses in automatizing repetitive manual tasks, saving time, money , as and other resources that can profit the business over the long term. In the wake of the advantages of technology, a lot of multinational companies like Accenture, IBM, Infosys, Deloitte, TCS, Capgemini and many others are using RPA to increase speed and precision. Even SMEs are spending money on RPA and are moving toward automation. In 2022 90% of the largest enterprises around the world will have adopted RPA. RPA will reach “near universal acceptance” within the five years to come. Rapid adoption of technology is creating huge jobs for highly skilled workers.
- Demand shortage of skilled manpower
Don’t believe the stories that RPA will eliminate jobs. In reality 52 percent of experts believe RPA will result in the creation of many new jobs in the year 2025. Due to the rapid growth of RPA firms require experienced RPA experts. According to NASSCOM that, the majority of world’s companies are currently facing an enormous need of RPA specialists in India.
Not only a job, but you will also earn a great pay as the annual salary of RPA developers can range between 4 lakh to Rs. 4 lakh up to Rs. 11,500 in India. The variance in salaries depends on three elements namely place of work, experience, and function.
Reason 3: Easy to understand and to implement
RPA is fairly simple to understand and to implement. It is relatively easy to learn and implement. RPA there are a variety of technical and non-technical roles like Process Designer, Automation Architect Project Manager Analyst, Business Analyst, Process SME, RPA Developer and many others to pick from. RPA technology is known as low-code/no-code technology.
There are few fundamental abilities like analytical thinking and problem solving and experience in the development of applications, API integration, data analytics that you should master to begin an profession in RPA. They are also easy to learn with the right type of instruction. In order to master the basics, it is recommended to have a solid understanding at a minimum of the most well-known automation tools, such as Blue Prism, Automation Anywhere and many more.
How do you make a name for yourself in RPA?
If you now have a clear idea of why you should make your career in RPA and you are thinking about where to begin? The development of the necessary capabilities and skills is the first step toward establishing your career in RPA. It is important to build the fundamentals , beginning by receiving top-quality instruction in important RPA tools like Blue Prism or Automation Anywhere.
There are many programs, certifications and resources that are available in a hybrid learning formats that include live classes that are interactive and online, taught by Industry Experts and self learning material. You can also participate in RPA hackathons and competitions that can help you gain practical knowledge.
These certifications are global and target the next generation of professionals. These certification programs ensure that you have the necessary training in RPA before you can enter the workforce. Many of these programs help you get a job in the top companies.




















Recent Comments